Cybersecurity Bingo
Meetings, especially in the cybersecurity realm, can sometimes feel like a stroll through a jargon jungle. There's a lot of "phishing" but not the kind that requires a fishing rod. There's talk of "firewalls," but nobody's trying to keep warm. To make our ventures through this linguistic labyrinth a tad more enjoyable, I've created a Cybersecurity Bingo Card. Loaded with popular terminologies—from the straightforward "DNS" to the all-too-relatable "Sorry, was on mute"—this card will help you decode the tech talk and bring a competitive edge to your meetings. Remember to play fair: no "proxy" players allowed, and don't just mark "threat" because someone side-eyed you for stealing the last donut. Dive in, have fun, and may the best jargon-juggler win!
LAPSUS$ and the Rising Tide: Navigating the Murky Waters of Insider Threats
Ransomware attacks are no longer just about encrypting data. They've morphed into a more sinister strategy: stealing data from substantial companies and then hanging the threat of its public release over their heads unless a hefty ransom is settled. More often than not, these criminals demand payment in cryptocurrencies like Bitcoin.
Empowering Cyber Defense: The Role of ChatGPT in Modern Cybersecurity
Cybersecurity is a critical concern for individuals, businesses, and governments alike, as the number of online threats continues to grow and evolve. With the rise of artificial intelligence, one tool that has the potential to have a significant impact on cybersecurity is ChatGPT.
The rising threats of IoT devices to election, healthcare, and energy infrastructure
Internet of Things (IoT) devices such as fitness trackers and home security cameras are growing in popularity, but many people don’t realize that these devices can also be used to attack critical infrastructure. In 2017, a group of hackers used IoT devices to launch a massive attack on the internet infrastructure provider Dyn, and they were only able to do this because they were able to exploit devices that were using default passwords.
Defense-in-Depth: A Multi-Layered Cybersecurity Approach
As the world becomes increasingly digitized, the risk of cyberattacks against businesses, governments, and individuals alike has increased dramatically. Hackers can gain access to sensitive data, steal identities or financial information, or damage computer networks and critical infrastructure.
Jumpstarting Your Journey in Cybersecurity: A Comprehensive Guide for Aspiring Professionals
Cybersecurity is a rapidly growing field, with a high demand for professionals who can protect against online threats and ensure the privacy and security of sensitive information. If you're interested in starting a career in cybersecurity, here are some steps to help you get started.
An Overview of the 16 Critical Infrastructure Sectors: Keeping Our Nation Secure
Critical infrastructure refers to those vital systems, networks, and assets whose incapacitation or destruction would have a debilitating effect on national security, the economy, public health, or any combination thereof. In the U.S., the Department of Homeland Security (DHS) has demarcated 16 specific critical infrastructure sectors. These sectors serve as the pillars that support the nation's day-to-day operations and its citizens' way of life.
Unveiling My Black Hat 2023 Presentations
I am delighted to announce the titles of my upcoming presentations for Black Hat 2023, both scheduled for August 10th. Here's a glimpse into what you can expect.
Join Me at Austin's Startup Week: A Deep Dive into Insider Threats and Neural Networking
Austin Startup Week, since its inception in 2011, has always been a vibrant tapestry of Austin's entrepreneurial spirit. A unique confluence of entrepreneurs, local leaders, and enthusiasts, it offers a rich platform to connect, collaborate, and grow. This year marks the 13th iteration of this celebrated event, which will span from November 6-10, 2023. From enlightening sessions, hands-on workshops, to dynamic startup showcases and networking mixers, Austin Startup Week promises to be an engaging experience. To all those who celebrate the spirit of innovation and entrepreneurship, I wholeheartedly encourage you to register and be a part of this distinctive celebration of Austin's diverse community of trailblazers.
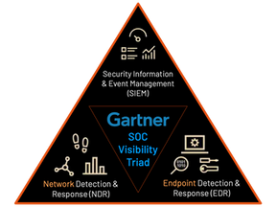
EDR and NDR
Two of the most important aspects of cybersecurity are network detection and response (NDR) and endpoint detection and response (EDR). While on the surface, there may appear to be similarities between the two, there are some key differences.