ManageEngine ADAudit Plus Vulnerability
While exploring the security aspects of ManageEngine ADAudit Plus, I discovered a security vulnerability (CVE-2023-32783) that may have far-reaching implications for other product users.

My findings indicate that ADAudit Plus contains a vulnerability which allows Windows user accounts to remain completely invisible to ADAudit Plus. User accounts leveraging this vulnerability will be undetected by ADAudit Plus, and all audit and security events raised by that user will be missed (i.e., Windows accounts logging in successfully or unsuccessfully). This vulnerability poses a potentially significant risk to organizations relying on ADAudit Plus to perform audit, compliance, and security functions accurately.
Following responsible disclosure guidelines, I secured the CVE but withheld public disclosure of the vulnerability for 90 days, allowing ManageEngine adequate time to address the issue or work with me on a timeline. Unfortunately, despite communication attempts, I could only get them to acknowledge but couldn't get them to provide any updates or collaborate. The 90-day disclosure period has expired, and this CVE is now public.
Steps to Reproduce
1. Setup:
- Install ManageEngine ADAudit Plus (Version: 7.1.1) on a Windows machine to monitor Windows Event Log activity for user accounts (e.g., a domain controller or event forwarding server).
- Access the ADAudit Plus portal page at http://localhost:8081.
- Navigate to the Reports section and select "User Logon Activity" (or any other report screen that displays user activities).
2. Execution:
- Carry out actions that trigger the generation of Windows event logs, such as logging into machines using domain accounts, locking screens, attempting logins with incorrect passwords, etc. ADAudit Plus will successfully detect all these activities, as advertised.
3. Exploit:
- Create a new user account on any machine that will generate Windows Event Logs to be observed by ADAudit Plus. Ensure the user account ends with a "$" symbol (e.g., "duser$").
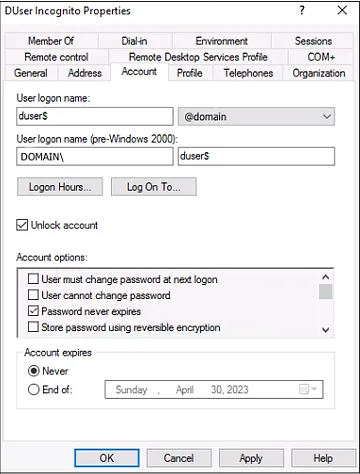
- Log in using this new account (in this example, "duser$") and perform various actions that result in creating Windows Event Logs.
- Observe that the ADAudit Plus portal does not recognize this user, and any actions taken by the user (whether successful or not) do not appear in any of the user or activity reports.
- Note that any user previously observed by ADAudit Plus will become invisible if they rename their user login to end with a '$' symbol.
Threat Vector
A malicious user, whether internal or external to the organization, aware of this vulnerability can create a new user account or rename an existing user account to have a $ suffix, and then move undetected across different machines and perform different actions that are all undetected by ADAudit Plus.
Severity: "Medium to High"
Rated "Medium to High" for the following reasons:
- This product is extensively utilized by organizations that depend on its accurate execution of audit, compliance, and security tasks.
- The simplicity of exploitation
- The potential impact on an organization's threat detection capabilities, given the possible invisibility of an adversary
- Suspected Issue and Proposed Solution
Suspected Issue and Proposed Solution
Windows Event Logs are notoriously challenging to work with, leading to a demand for products that can filter out the noise and extract meaningful information. I suspect the ADAudit Plus code may examine event properties, match the “TargetUserName,” and disregard any entry ending with a "$." AD Audit Plus incorrectly assumes that such entries only represent system accounts leading to the vulnerability described. Consequently, a legitimate Windows user account (non-system) would be invisible to the product.
The solution would be to avoid relying on the "$" suffix to identify system accounts. This would distinguish user accounts from system accounts more accurately.










