LAPSUS$ and the Rising Tide: Navigating the Murky Waters of Insider Threats
Ransomware attacks are no longer just about encrypting data. They've morphed into a more sinister strategy: stealing data from substantial companies and then hanging the threat of its public release over their heads unless a hefty ransom is settled. More often than not, these criminals demand payment in cryptocurrencies like Bitcoin.
The rising threats of IoT devices to election, healthcare, and energy infrastructure
Internet of Things (IoT) devices such as fitness trackers and home security cameras are growing in popularity, but many people don’t realize that these devices can also be used to attack critical infrastructure. In 2017, a group of hackers used IoT devices to launch a massive attack on the internet infrastructure provider Dyn, and they were only able to do this because they were able to exploit devices that were using default passwords.
Defense-in-Depth: A Multi-Layered Cybersecurity Approach
As the world becomes increasingly digitized, the risk of cyberattacks against businesses, governments, and individuals alike has increased dramatically. Hackers can gain access to sensitive data, steal identities or financial information, or damage computer networks and critical infrastructure.
Jumpstarting Your Journey in Cybersecurity: A Comprehensive Guide for Aspiring Professionals
Cybersecurity is a rapidly growing field, with a high demand for professionals who can protect against online threats and ensure the privacy and security of sensitive information. If you're interested in starting a career in cybersecurity, here are some steps to help you get started.
Breaking it Down: Black Hat vs. DEFCON - Which Cybersecurity Conference is Right for You?
The world of cybersecurity is vast and ever-changing. As technology continues to advance, the need for skilled professionals who can keep up with new developments and protect against evolving threats is crucial. One way to stay current and informed is to attend cybersecurity conferences, where you can learn about the latest trends, tools, and best practices. Two of the most popular conferences in the cybersecurity world are Black Hat and DEFCON. In this blog post, we'll explore the key differences between these two events and help you determine which one is right for you.
An Overview of the 16 Critical Infrastructure Sectors: Keeping Our Nation Secure
Critical infrastructure refers to those vital systems, networks, and assets whose incapacitation or destruction would have a debilitating effect on national security, the economy, public health, or any combination thereof. In the U.S., the Department of Homeland Security (DHS) has demarcated 16 specific critical infrastructure sectors. These sectors serve as the pillars that support the nation's day-to-day operations and its citizens' way of life.
Unveiling My Black Hat 2023 Presentations
I am delighted to announce the titles of my upcoming presentations for Black Hat 2023, both scheduled for August 10th. Here's a glimpse into what you can expect.
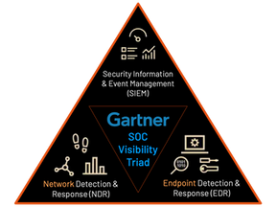
EDR and NDR
Two of the most important aspects of cybersecurity are network detection and response (NDR) and endpoint detection and response (EDR). While on the surface, there may appear to be similarities between the two, there are some key differences.
Cyberspace Solarium Commission Report
In 2019, I was honored to be asked to participate in the Cyberspace Solarium Commission (CSC), a significant initiative established in the United States as part of the National Defense Authorization Act for Fiscal Year 2019. The Commission released its report in 2020, which included a wide range of recommendations for both legislative and executive actions.
"Do You Have a Safe Word Yet?" A Call to Arms Against Deep Fake Voice Attacks
In the digital age, we've seen a steady evolution of threats, but none perhaps as chilling as the rise of deep fake voices and videos. Malicious actors can, with relative ease, use voice technology to mimic someone's voice and use it in criminally exploitative ways—from convincing others to take potentially dangerous actions, to making fraudulent payments, or opening gaps in security. This is a threat too severe to overlook. So, how do we safeguard ourselves in a landscape where our ears can't always be trusted?